Threat Advisory
Description

This vulnerability exists in Microsoft Office & Windows HTML due to insufficient validation of user-supplied input when handling cross-protocol file navigation. An attacker could exploit this vulnerability by persuading a victim to open a specially crafted file.
Successful exploitation of this vulnerability could allow a remote attacker to execute arbitrary code on the targeted system
Mitigations

Customers who use Microsoft Defender for Office are protected from attachments that attempt to exploit this vulnerability. In current attack chains, the use of the Block all Office applications from creating child processes Attack Surface Reduction Rule will prevent the vulnerability from being exploited.
Organizations who cannot take advantage of these protections can add the following application names to this registry key as values of type REG_DWORD with data 1.:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION
- Excel.exe
- Graph.exe
- MSAccess.exe
- MSPub.exe
- PowerPoint.exe
- Visio.exe
- WinProj.exe
- WinWord.exe
- Wordpad.exe
Solution:
Apply appropriate security updates as mentioned in the below link
You can locate the registry key FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION by following these steps:
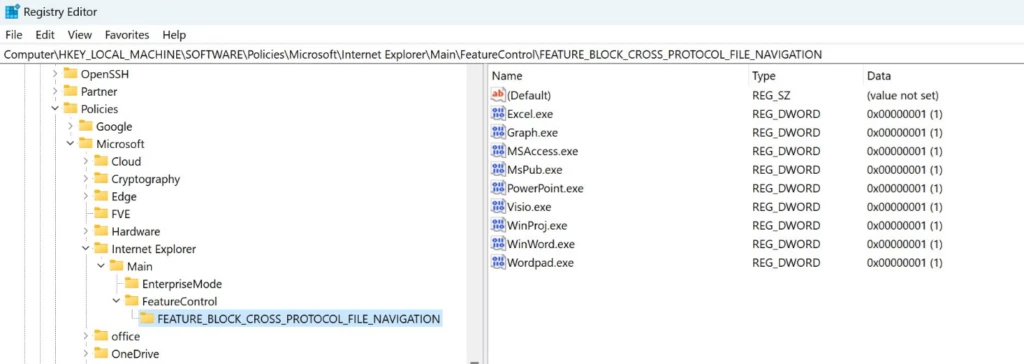
- Press the Windows key + R to open the Run dialog box.
- Type “regedit” (without quotes) and press Enter.
- In the Registry Editor window, navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl.
- If you cannot find FeatureControl, right-click on Main and select New > Key. Name the new key FeatureControl.
- Right-click on FeatureControl and select New > Key. Name the new key FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION.
- Right-click on FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION and select New > DWORD (32-bit) Value.
- Name the new value after your executable file (e.g., contoso.exe).
- Double-click on the new value and set its data to 1.